802.1x ON LINUX/WINDOWS CLIENT WITH NPS
- Celal
- Apr 12, 2021
- 3 min read
Updated: Apr 11, 2022
I made the first 802.1x configuration at a Natural gas firm in 2006. Not much has changed since then. Only the component’s version of 802.1x has changed. If you have a Windows server, Supplicant and 802.1x supported switch, these are enough for 802.1x configuration. You can find thousands of samples on the internet. I will configure machine auth with NPS for the Windows client. Why is machine authentication important? Let’s think about it. You assume that you connect your desktop PC in your company from home with RDP and you didn’t log in with any username and password. You won't access your desktop pc. Why? Because the system waits for login with user/pass information for opening port. What can I do about this? Of course, I will use machine authentication. Also, I will try user authentication for Linux machines.
Let's shortly talk about PEAP Before I start to configure. Why do we use PEAP authentication for 802.1x? Because PEAP is secure and more manageable than EAP-TLS. Sometimes we have devices other than Windows machines. for example Linux machine. Linux machines support 802.1x but we can't able to enroll in the Active directory.
If you use PEAP, the client verifies if the server is trusted. The server does not verify if the client is trusted. In Contrast, EAP-TLS checks both side certificates to have. Therefore, we will not be dealing with certification on the Linux side. But the Windows client-side certificate will be validated because of machine authentication.
Not: TEAP is a tunnel-based Extensible Authentication Protocol method that establishes a secure tunnel and executes other EAP methods under the protection of that secured tunnel. we can use the TEAP authentication if you want to use both authentication methods together (EAP and PEAP).
We will configure it according to the below topology;

I'll start with the switch configuration.
Switch Config;
aaa new-model
aaa authentication dot1x default group radius
aaa accounting dot1x default start-stop group radius
interface Ethernet0/3
switchport access vlan 10
switchport mode access
authentication port-control auto
dot1x pae authenticator
interface Ethernet1/2
switchport access vlan 10
switchport mode access
authentication port-control auto
dot1x pae authenticator
radius server RAD1
address ipv4 20.20.20.20 auth-port 1645 acct-port 1646
key cisco1231-Windows Server Preparation ;
I will bypass the installation of NPS and Certificate Authority. Only I will show how to configure these.
a-) NPS Client Configuration;
I add the switch as 802.1x client. Radius Client >Right Click>New


b-)Windows User and Group Configuration;
I will use machine authentication for Windows clients. For this I will create a computer group(Elma-Computer) for the machines which are attached to the domain and I will enroll the machine in this group.

I will use user authentication for Linux clients. For this, I will create a user. This user will be Domain users as default

c-) NPS Network Policies Configuration;
Write the network policy; Network Policies>Right Click>New
This configuration is for Windows machine authentication.




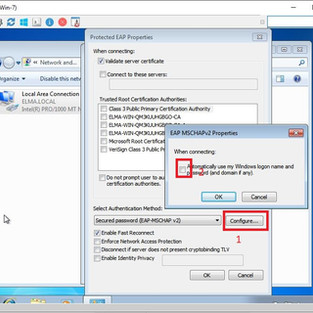
Select the authentication type as PEAP

Radius Server automatically takes certificates from CA. this certificate has a duration of one year.
if you want it to be extended automatically. This link will be useful to you.

We define the restrictions.

Radius attributes are very important. These attributes can be used to define authorization. But I won't use it. I will try only for authentication.

Network Policy is finished.
We have finished the configuration for the Win machine. I configure 802.1x for Linux machines. Unlike the operations, I have done above. Just create a new policy and this time select the domain user.

After the configuration is completed we have two policies. One of them is for Windows machines, other is for domain users.

2-)Windows-7 Client Preparation;
I will take the win-7 client to ELMA.LOCAL domain.
Our win-7 client is ready for 802.1x configuration;
IAS log viewer is the best tool to view NPS logs.
You will see that the Win machine is authenticated.

Also, you will see it as authenticated in the port's detail.

3-)Linux-Ubuntu Preparation;

You know I have mentioned the PEAP and the client does not need certification at the client-side.

Linux client is succeeded.

If we examine the NPS log with the IAS Log Viewer program. you will see the Linux user is access granted by the server.


Thanks for Reading.