S2S VPN ERRORS BETWEEN CISCO ASA & FORTINET
- Celal
- Feb 13, 2021
- 4 min read
Updated: Mar 13, 2022
Sometimes while I install the site-to-site IPsec between VPN boxes, I'm getting some error that everyone generally come upon. I wanna write these errors. I hope this post is useful for new beginners.
I will examine the error messages according to the topology below.

ERROR-1:
Routing failed to locate next hop for udp from NP Identity Ifc:188.18.17.1/62465 to mpls:3.3.3.1/62465
IKEv1 was unsuccessful at setting up a tunnel. Map Tag = mpls_map. Map Sequence Number = 2
ERROR-2:
Tunnel Manager has failed to establish an L2L SA. All configured IKE versions failed to establish the tunnel. Map Tag= mpls_map. Map Sequence Number = 2.
IKEv1 was unsuccessful at setting up a tunnel. Map Tag = mpls_map. Map Sequence Number = 2.
THE SOLUTION OF ERROR-1,2:
These errors say that there is a big wrong in our configuration. This is a reachability problem between VPN boxes. if we have two exits points. Related routes might not be written to the correct point in our VPN boxes. Sometimes we are typing the wrong subnet mask. For my example; Now I'm writing route to the correct point. If the route is not written to the correct point, the IPsec tunnel will be tried to install over the internet interface because of the default route. For this is not to happen, we have to write the route to Mpls interface on both devices so they can access each other.
Add the IP address of the Fortinet to ASA's routing table.

Or add the IP address of the ASA to Fortinet's routing table.

Here is the result;
Group = 3.3.3.1, IP = 3.3.3.1, PHASE 1 COMPLETED
Tunnel Manager dispatching a KEY_ACQUIRE message to IKEv1. Map Tag = mpls_map. Map Sequence Number = 2.
Group = 3.3.3.1, IP = 3.3.3.1, IKE Initiator: New Phase 2, Intf mpls, IKE Peer 3.3.3.1 local Proxy Address 20.20.20.0, remote Proxy Address 192.168.60.0, Crypto map (mpls_map)
Group = 3.3.3.1, IP = 3.3.3.1, Security negotiation complete for LAN-to-LAN Group (3.3.3.1) Responder, Inbound SPI = 0xaa2c7b53, Outbound SPI = 0x67ee5d0a
IPSEC: An outbound LAN-to-LAN SA (SPI= 0x67EE5D0A) between 188.18.17.1 and 3.3.3.1 (user= 3.3.3.1) has been created.
IPSEC: An inbound LAN-to-LAN SA (SPI= 0xAA2C7B53) between 188.18.17.1 and 3.3.3.1 (user= 3.3.3.1) has been created.
Group = 3.3.3.1, IP = 3.3.3.1, PHASE 2 COMPLETED (msgid=22e90ccb)
IKEv1 was successful at setting up a tunnel. Map Tag = mpls_map. Map Sequence Number = 2.
ERROR-3:
Phase 1 failure: Mismatched attribute types for class Group Description: Rcv'd: Group 5 Cfg'd: Group 2
Group = 3.3.3.1, IP = 3.3.3.1, Duplicate Phase 1 packet detected. Retransmitting last packet.
IKEv1 was unsuccessful at setting up a tunnel. Map Tag = mpls_map. Map Sequence Number = 2.
THE SOLUTION OF ERROR-3:
İf you are getting the error that is a mismatched attribute in PHASE 1. You first have to check the ike pre-share key. The pre-shared key may not be matched on both sides.
ERROR-4;
IP = 3.3.3.1, Error processing payload: Payload ID: 1
IKEv1 was unsuccessful at setting up a tunnel. Map Tag = mpls_map. Map Sequence Number = 2.
THE SOLUTION OF ERROR-4:
A packet has been received with a payload that cannot be processed. Generally, This error comes up when the IKE policy does not match on both peers. So this is related to PHASE-1. We must fix policies on both sides.
Cisco ASA side;

Fortigate Fw side;

ERROR-5:
Group = 3.3.3.1, IP = 3.3.3.1, IKE Initiator: New Phase 2, Intf mpls, IKE Peer 3.3.3.1 local Proxy Address 20.20.20.0, remote Proxy Address 192.168.60.0, Crypto map (mpls_map)
Group = 3.3.3.1, IP = 3.3.3.1, Received non-routine Notify message: No proposal chosen (14)
Group = 3.3.3.1, IP = 3.3.3.1, QM FSM error (P2 struct &0x00007fffce4c3170, mess id 0x92bb8655)!
IKEv1 was unsuccessful at setting up a tunnel. Map Tag = mpls_map. Map Sequence Number = 2.
Group = 3.3.3.1, IP = 3.3.3.1, PHASE 1 COMPLETED

THE SOLUTION OF ERROR-5;
The keywords are for us; Received non-routine Notify message: No proposal chosen. The error says where is wrong in our configuration. This error is in phase-2 because phase-1 is completed. The meaning of No proposal may be related IPSEC encryption list.
Cisco ASA side;

Fortinet FW side;

If you set the proper encryption algorithm in both VPN boxes. The problem will be solved.
ERROR-6:
Group = 3.3.3.1, IP = 3.3.3.1, Received non-routine Notify message: No proposal chosen (14)
Group = 3.3.3.1, IP = 3.3.3.1, QM FSM error (P2 struct &0x00007fffce4d4ac0, mess id 0xf37ec058)!
Group = 3.3.3.1, IP = 3.3.3.1, PHASE 1 COMPLETED
THE SOLUTION OF ERROR-6;
This error is almost the same as Error-5. Phase-1 is completed but Phase-2 is not completed. The PFS is enabled on Fortinet Fw but is disabled on Cisco ASA. I have to change as to enable on Cisco.

ERROR-7:
Group = 3.3.3.1, IP = 3.3.3.1, QM FSM error (P2 struct &0x00007fffcda24c00, mess id 0x3be33942)!
Group = 3.3.3.1, IP = 3.3.3.1, Removing peer from correlator table failed, no match!
IKEv1 was unsuccessful at setting up a tunnel. Map Tag = mpls_map. Map Sequence Number = 2.
Group = 3.3.3.1, IP = 3.3.3.1, PHASE 1 COMPLETED
THE SOLUTION OF ERROR-7;
There is no proposal like in error-5,6. This error is related to phase-2. You have to check the ISAKMP and crypto map configuration on both peers. My problem is the wrong local subnet on Fortinet Fw In my configuration.

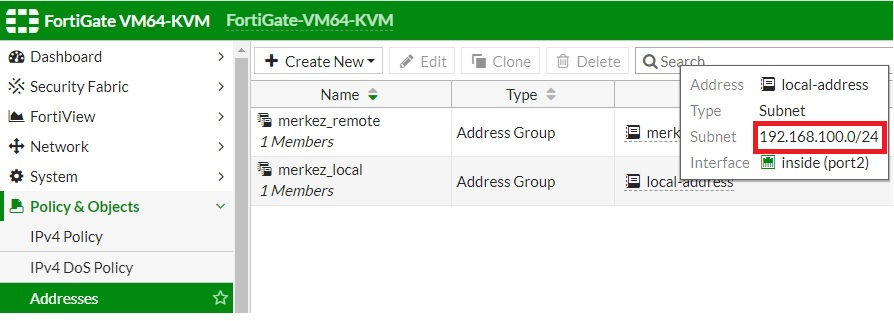
ERROR-8:
Local:188.18.17.1:500 Remote:3.3.3.1:500 Username:Unknown IKEv2 Received a IKE_INIT_SA request
Local:188.18.17.1:500 Remote:3.3.3.1:500 Username:Unknown IKEv2 Negotiation aborted due to ERROR: Failed to find a matching policy
THE SOLUTION OF ERROR-8:
If we get this error. There is a conflict in IKE versions. We have to set the same IKE version.
ERROR-9:
3Jun 30 202109:03:39713061Group = 3.3.3.1, IP = 3.3.3.1, Rejecting IPSec tunnel: no matching crypto map entry for remote proxy 192.168.60.0/255.255.255.0/0/0 local proxy 0.0.0.0/0.0.0.0/0/0 on interface mpls
THE SOLUTION OF ERROR-9:
You know, the policies should be the same on both sides. When I look at the Fortigate side, I see that the remote network is marked as all. The only required network should be marked on both sides.
Fortinet;

The remote address should be changed with 20.20.20.0/24
Asa;

I hope that will be useful.
Thanks for Reading


I love the 'one-tap' connect feature. No annoying ads or confusing settings, just a clean interface that does exactly what it's supposed to do. It’s very lightweight and doesn't slow down my phone. Grab it here: https://captain-droid.com/en/apps/tools/vpn-quark/ — perfect for anyone who values simplicity!